What is a Merkle Tree?
Today’s Bullets:
1) What is a Hash?
2) What is a Merkle Tree?
3) Merkle Tree Proof of Reserves
We will soon start to hear a lot more about Merkle Trees and their capacity to verify reserves on an exchange or other decentralised platform, given all the dubious and outright criminal activity we've seen in the cryptocurrency industry lately.
But what precisely is a Merkle Tree, and do they serve as a foolproof (or crookproof, as the case may be) manner of demonstrating your balances?
I'm not a programmer, and I assume you aren't either. In order to make you a little smarter about the collateral side of the decentralised world, let's take it slow and simple today.
#️⃣ What is a Hash?
To start, and in the most basic terms of the cryptography world, a secure hash algorithm or SHA, is a mathematical formula that transforms and compresses a string of data from any size into a fixed-size that is completely different than the original data.
The most common place we see the use of hashes is in the encryption of passwords. This way, the server that’s checking the password only has to keep track of a user’s hash value, rather than the actual password itself. So, if a company’s database is hacked, it will only reveal the hashes and not the actual passwords.
Hashes can be extremely effective because of what is called the avalanche effect, where the change of just a few characters being encrypted can produce a huge change in the output value.
Notice in the example below how the output values are all the same size, but completely different.
As a note, Bitcoin uses SHA-256, a hash function within the SHA-2 (Secure Hash Algorithm 2) family. SHA-256 was developed by the NSA in 2016 to solve problems with SHA-1.
SHA-256 has never been compromised and is an extremely secure cryptographic hash function. As a result, it's one of the most popular cryptographic hash functions in the cryptocurrency world.
Created to be a one-way street of information, hash functions, and SHA-256 in particular, make it impossible to recreate a hash’s input from the output.
SHA-256 and the Bitcoin network, is widely considered the most secure hash algorithm in the world.
Which brings us to the hash tree, or Merkle Tree.
🌳 What is a Merkle Tree?
First, a Merkle Tree is simply a hash tree, a concept patented by Ralph Merkle in 1979.
See, in decentralized, peer-to-peer transactions, data verification is imperative. With data being recording in numerous places all at once, if data is changed in one location, it must be changed everywhere.
And these changes must be verified to be consistent everywhere. But it can become overwhelming pretty quickly to check the entirety of every single file across an entire system when checking for consistency.
But we can use hashing to minimize the amount of data that needs to be checked, right?
Turn data into hashes and list those instead (just like passwords).
Exactly. And this is where the Merkle or hash tree comes into play.
Basically, hash trees allow us to verify data stored or transferred in and between computers in a peer-to-per network by ensuring blocks sent between peers are received unaltered and undamaged.
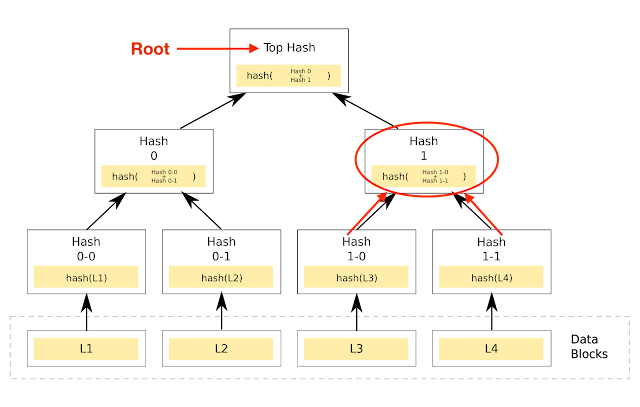
A hash tree is a tree of hashes (see below) in which the leaves (or leafs or leaf nodes) are hashes of blocks of data in a file. Nodes toward the top of the tree are hashes of their respective children.
For example, hash 1 is the result of hashing the concatenation (fancy computer programming word for combination) of the two hashes below it on the tree.
I.e., Hash 1 = Hash (hash 1-0 + Hash 1-1)
See Red Circle Below
Sitting at the very top of the tree is what is called the top hash (aka root). This top hash allows any part of the hash tree to be received from any non-trusted source, like a peer-to-peer network.
Then, any received branch, etc. can be checked against the trusted top hash for verification, to see if the hash is damaged or even fake.
In other words, instead of sending an entire file over the network, we can just send a hash of the file, and checking it against the root tells us if it has been compromised.
✅ Merkle Tree Proof of Reserves
In traditional financial accounting, we use books and records and balance sheets. A balance sheet shows what a company owns and what it owes, as a summary. The books and records show all the transactions that add up to the balance sheet.
All these books and records and balance sheets, etc. are reviewed and verified by a third party.
The auditor.
And if an auditor finds something that doesn’t add up, they will flag it and refuse to vouch for the validity of the books until the discrepancy is resolved.
So, if you deposit money with a traditional bank, say JP Morgan, there is a pretty clear record of you sending money from your bank to JP Morgan and hence a liability on their books to you.
JP Morgan’s account managers, accountants, comptrollers, CFO, and auditors all agree that your deposit is there and JP Morgan owes that to you.
But what about decentralized exchanges without the same human monitored chain of custody and account oversight?
If you sent a Bitcoin to Binance, for instance, how can you tell your deposit, a few hours, days, or months later are still there? That they weren’t lent out or moved by a bad actor?
It would seem absurd for Binance to publish a list of every single balance of every account so individuals could check their balance against it, right?
Small privacy problem there.
So, what’s the solution?
You got it. The Merkle Tree.
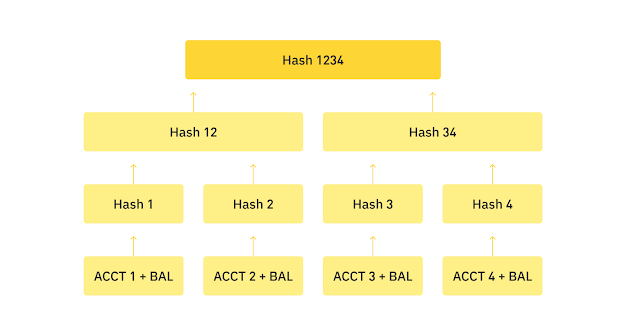
And so Binance just announced they will be using a Merkle Tree to verify assets are 1:1 and “allow people to verify their assets within the platform.”
Here’s a photo of the Merkle Tree that Binance now has on the Proof of Reserves page of their website:
And the instructions: Log in to the Binance website, Click on Wallet, Click on Audit, and find your Merkle Leaf and Record ID within the page.
Awesome. So you can check that your balances are indeed still there, and that they have not been moved or misappropriated.
All good. The verification of reserves problem is solved, end of story, right?
Right?
credit: James Lavish
That’s it. I hope you feel a little bit smarter knowing about Merkle Trees, how they work, and their limitations. And I hope you’re inspire to take possession of your own assets.


Comments
Post a Comment